In today's digital landscape, safeguarding client data is paramount. This guide delves into the strategies and best practices to ensure the security of client information using Digital Ocean. From encryption methods to access control measures, we explore how businesses can protect sensitive data effectively.
Introduction to Securing Client Data with Digital Ocean
In today's digital age, the protection of client data is paramount for businesses to maintain trust and credibility. With cyber threats on the rise, ensuring the security and confidentiality of sensitive information has become a top priority for organizations across industries.
This is where hosting providers like Digital Ocean play a crucial role in offering secure solutions to safeguard valuable data.
The Role of Digital Ocean in Providing Secure Hosting Solutions
Digital Ocean is a leading cloud infrastructure provider known for its robust security measures and reliable services. By offering features such as data encryption, firewalls, and regular security updates, Digital Ocean ensures that client data remains protected from unauthorized access and cyber attacks.
Their focus on compliance with industry standards and regulations further enhances the security of hosted data, giving businesses peace of mind when it comes to confidentiality and integrity.
The Significance of Data Protection for Businesses
Data protection is not just a legal requirement but also a critical aspect of maintaining a positive reputation and avoiding costly data breaches. Businesses that fail to secure client data risk financial losses, legal consequences, and damage to their brand image.
By investing in secure hosting solutions like those offered by Digital Ocean, organizations can mitigate these risks and build a strong foundation for trust with their clients. Prioritizing data protection is essential for long-term success in today's competitive and data-driven business landscape.
Data Encryption Best Practices
Data encryption is a crucial method used to secure client data by converting the information into a code that can only be accessed with the proper decryption key. This ensures that even if unauthorized users gain access to the data, they will not be able to decipher it without the encryption key.
This adds an extra layer of security to sensitive information and helps prevent data breaches.
Encryption Methods for Data Protection
- Advanced Encryption Standard (AES): AES is a symmetric encryption algorithm widely used for securing sensitive data. It is highly secure and efficient, making it a popular choice for protecting client information.
- Rivest-Shamir-Adleman (RSA): RSA is an asymmetric encryption algorithm that uses a public key for encryption and a private key for decryption. This method is commonly used for securing data during transmission.
- Triple Data Encryption Standard (3DES): 3DES is a symmetric encryption algorithm that applies the Data Encryption Standard (DES) cipher three times to increase security. While not as efficient as AES, it is still a reliable method for data protection.
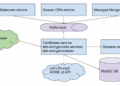
Digital Ocean’s Encryption Practices
Digital Ocean prioritizes data security by implementing encryption at various levels. They use AES-256 encryption to safeguard data at rest, ensuring that stored information remains secure. Additionally, data transferred between users and Digital Ocean services is encrypted using TLS/SSL protocols, adding another layer of protection.
By following best practices in encryption, Digital Ocean maintains a secure environment for client data.
Secure Access Control Measures
Access control is a critical aspect of safeguarding client data, as it ensures that only authorized individuals can access sensitive information. Authentication and authorization play key roles in controlling data access, helping to prevent unauthorized users from viewing or modifying confidential data.
Role of Authentication
Authentication verifies the identity of users attempting to access a system or application. This process typically involves entering a username and password, biometric information, or a security token. By confirming the identity of individuals, authentication helps to ensure that only authorized users can access client data.
Role of Authorization
Authorization determines the level of access that authenticated users have within a system. This involves assigning permissions and privileges based on the user's role or responsibilities. By implementing authorization controls, organizations can limit the actions that users can perform, reducing the risk of data breaches or unauthorized access.
Access Control Models
There are different access control models that can be implemented on Digital Ocean to enhance data security. Some common models include:
- Discretionary Access Control (DAC): Allows users to set access permissions for their own resources.
- Mandatory Access Control (MAC): Enforces access policies set by system administrators, restricting user control.
- Role-Based Access Control (RBAC): Assigns permissions based on the user's role within the organization, simplifying access management.
Each of these models offers unique advantages and can be tailored to suit the specific security requirements of an organization using Digital Ocean's infrastructure.
Regular Data Backups
Regular data backups play a crucial role in ensuring the security and integrity of client data. In the event of data loss due to unforeseen circumstances such as cyber attacks, hardware failures, or human error, having up-to-date backups can help restore information and minimize the impact on your business operations.
Setting Up Automated Backups on Digital Ocean
- Log in to your Digital Ocean account and navigate to the Droplets section.
- Select the Droplet for which you want to set up backups.
- Click on the "Backups" tab and enable automated backups for the Droplet.
- Choose the backup frequency and retention policy according to your requirements.
- Save the changes, and Digital Ocean will now automatically create backups based on your settings.
Best Practices for Data Backup Frequency and Storage Options
- Regular Frequency: It is recommended to schedule backups daily or weekly, depending on the volume and importance of the data.
- Off-site Storage: Store backups in a separate location or cloud service to ensure data redundancy in case of a disaster affecting the primary site.
- Encryption: Encrypt the backup data to protect sensitive information from unauthorized access during storage and transfer.
- Monitoring and Testing: Regularly monitor backup processes and perform test restores to verify the integrity and accessibility of the backed-up data.
Network Security Protocols
Network security protocols play a crucial role in ensuring the confidentiality and integrity of client data during transmission over networks. By implementing robust protocols, organizations can safeguard sensitive information from unauthorized access and cyber threats.
SSL/TLS Protocols
- SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that establish secure connections between servers and clients.
- These protocols encrypt data during transmission, preventing interception and eavesdropping by malicious entities.
- SSL/TLS certificates validate the authenticity of websites, ensuring users are connecting to legitimate servers.
- Implementing SSL/TLS protocols is essential for securing sensitive data, such as personal information and financial transactions.
Digital Ocean’s Network Security
- Digital Ocean employs robust network security measures to protect clients' data stored on their servers.
- Firewalls, intrusion detection systems, and DDoS mitigation are used to prevent unauthorized access and cyber attacks.
- Regular security audits and compliance checks ensure that network security protocols are up to date and effective.
- Digital Ocean's commitment to maintaining a secure network infrastructure provides clients with peace of mind regarding the safety of their data.
Closing Summary
As we wrap up our discussion on securing client data with Digital Ocean, it's clear that prioritizing data protection is key for any business. By implementing the right measures and staying proactive, businesses can safeguard their clients' information and maintain trust in an increasingly digital world.
FAQ Section
How can encryption help secure client data?
Encryption scrambles data into a coded format that can only be accessed with the right decryption key, ensuring that sensitive information remains secure even if intercepted.
What are some common access control models for data security?
Common access control models include discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC), each offering different levels of data protection.
Why are regular data backups important?
Regular backups ensure that in the event of data loss or corruption, businesses can recover vital information and minimize disruptions to operations.
How does Digital Ocean ensure network security for client data?
Digital Ocean implements robust network security protocols like SSL/TLS to encrypt data during transmission, protecting it from unauthorized access or interception.






![5 Best eCommerce Marketing Digital Agencies [2024 Edition]](https://share.radartasik.id/wp-content/uploads/2025/08/Best-E-Commerce-Marketing-Agencies-2048x1024-1-120x86.jpg)