In the fast-evolving digital realm of 2025, the essence of secure digital identity protocols cannot be overstated. This introductory passage sets the stage for a profound exploration, promising a blend of insights and foresight that will captivate readers seeking to navigate the complexities of tomorrow's cyber world.
Delve into the risks and rewards, challenges and triumphs that lie ahead as we journey towards a future where digital identities are not just protected but fortified against the ever-looming threats of cyber breaches.
Importance of Safe Digital Identity Protocols in 2025
In the ever-evolving digital landscape of 2025, safe digital identity protocols play a crucial role in ensuring the security and privacy of individuals, organizations, and sensitive data. These protocols are designed to authenticate and verify the identities of users in online interactions, preventing unauthorized access and protecting against identity theft and fraud.
Significance of Secure Digital Identity Protocols
Implementing safe digital identity protocols is essential to safeguarding personal information and maintaining trust in online transactions. By establishing robust verification mechanisms, such as two-factor authentication and biometric identification, organizations can enhance security measures and protect against cyber threats.
Potential Risks of Not Implementing Safe Digital Identity Protocols
Failure to adopt secure digital identity protocols can expose individuals and businesses to a myriad of risks, including data breaches, identity theft, financial fraud, and reputational damage. Without proper authentication measures in place, cybercriminals can exploit vulnerabilities to gain unauthorized access to sensitive information, leading to severe consequences for victims.
Key Benefits of Robust Digital Identity Protection Measures
Having strong digital identity protection measures in place offers several benefits, such as increased security, reduced fraud, enhanced user trust, and regulatory compliance. By prioritizing the implementation of secure protocols, organizations can mitigate risks, protect confidential data, and uphold the integrity of their digital operations in an increasingly interconnected world.
Current Challenges in Implementing Safe Digital Identity Protocols
As we move towards implementing safe digital identity protocols in 2025, there are several challenges that need to be addressed to ensure the security and privacy of user information.
Obstacles Faced in Deploying Secure Digital Identity Protocols
- Resistance to Change: Organizations may be resistant to implementing new digital identity protocols due to the costs and resources involved in the transition.
- Interoperability Issues: Ensuring that different systems and platforms can communicate securely with each other can be a significant challenge.
- Regulatory Compliance: Meeting the various regulatory requirements related to data privacy and security can be complex and time-consuming.
Recent Cybersecurity Breaches Related to Weak Digital Identity Measures
- In 2021, the SolarWinds cyberattack compromised the digital identities of numerous government agencies and organizations, highlighting the risks of weak identity measures.
- The Colonial Pipeline ransomware attack in the same year exploited vulnerabilities in digital identity protocols, leading to a major disruption in fuel supply.
Complexities of Balancing Security with User Convenience in Digital Identity Systems
- Implementing strong security measures, such as multi-factor authentication, can sometimes create friction for users who prioritize convenience over security.
- Finding the right balance between robust security and seamless user experience is crucial to ensure widespread adoption of digital identity systems.
Emerging Technologies for Enhancing Digital Identity Security

In the rapidly evolving digital landscape of 2025, it is crucial to explore innovative technologies that can enhance the security of digital identities. Technologies like blockchain, biometrics, and artificial intelligence (AI) are at the forefront of strengthening digital identity protection.
Blockchain Technology
Blockchain technology, known for its decentralized and tamper-proof nature, is revolutionizing digital identity security. By storing identity information in a distributed ledger, blockchain ensures data integrity and reduces the risk of identity theft and fraud.
Biometric Authentication
Biometrics, such as fingerprint scans, facial recognition, and iris scans, offer a highly secure method of authentication. These unique biological characteristics provide a more reliable way to verify identity and prevent unauthorized access to sensitive information.
Artificial Intelligence in Authentication
AI-powered authentication systems can analyze user behavior patterns and detect anomalies in real-time. By continuously learning and adapting, AI enhances the accuracy of identity verification processes and helps to identify potential security threats.
Multi-Factor Authentication vs. Passwordless Solutions
Multi-factor authentication (MFA) combines multiple verification methods, such as passwords, biometrics, and OTPs, to add layers of security. On the other hand, passwordless solutions eliminate the need for passwords entirely, relying on biometrics or cryptographic keys for authentication. Both approaches offer enhanced security and convenience for users.
Decentralized Identity Platforms
Decentralized identity platforms empower individuals to control their own identity information without relying on centralized authorities. By leveraging blockchain technology and cryptographic principles, these platforms ensure privacy, security, and data ownership for users in the digital realm.
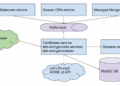
Regulatory Frameworks and Compliance Standards
In the realm of digital identity protocols, regulatory frameworks and compliance standards play a crucial role in ensuring the security and privacy of user data. These guidelines are designed to protect individuals' personal information and prevent unauthorized access or misuse.
Existing Data Protection Regulations
- The General Data Protection Regulation (GDPR): Enforced by the European Union, GDPR sets strict guidelines for the collection, processing, and storage of personal data. It emphasizes transparency, consent, and the right to erasure.
- The California Consumer Privacy Act (CCPA): Implemented in California, CCPA gives consumers more control over their personal information held by businesses. It requires transparency about data collection practices and allows users to opt-out of data selling.
Challenges of Maintaining Compliance
- Complexity and Variability: With data privacy laws evolving rapidly, organizations find it challenging to keep up with changing regulations across different regions.
- Cost and Resources: Achieving compliance with multiple regulatory frameworks requires significant investments in technology, training, and legal resources.
- Data Localization Requirements: Some regulations mandate that data must be stored within specific geographic locations, adding complexity to cross-border data transfers.
- Third-Party Compliance: Ensuring that third-party vendors and partners also adhere to regulatory standards can be a daunting task for organizations.
User Experience Considerations in Secure Digital Identity Solutions
User-centric design is crucial in the development of digital identity systems to ensure a seamless and secure experience for users. By prioritizing the needs and preferences of users, organizations can enhance trust and usability while maintaining high levels of security.
Finding the right balance between usability and security is key to successful implementation of digital identity protocols.
Importance of User-Centric Design
Creating digital identity solutions with a user-centric design approach is essential for increasing user adoption and satisfaction. By focusing on the needs, expectations, and behaviors of users, organizations can create intuitive and easy-to-use interfaces that encourage users to engage with the system.
Strategies for Seamless User Authentication Experiences
Implementing strategies such as biometric authentication, multi-factor authentication, and passwordless authentication can enhance security without compromising user experience. By offering a variety of authentication methods, organizations can cater to different user preferences while maintaining a high level of security.
Balance between Usability and Security
Finding the right balance between usability and security is crucial in implementing digital identity protocols. Organizations must prioritize user experience without sacrificing security measures. This can be achieved through user testing, feedback collection, and iterative design improvements to ensure a seamless yet secure digital identity solution.
Future Trends in Safe Digital Identity Protocols
As technology continues to evolve rapidly, the future of safe digital identity protocols is likely to see significant advancements in various areas. From the impact of quantum computing to the role of machine learning and the concept of self-sovereign identity, the landscape of digital identity management is set to undergo transformation.
Advancements in Quantum Computing
Quantum computing has the potential to revolutionize digital identity security by enabling faster and more efficient cryptographic processes. With the ability to perform complex calculations at a speed that surpasses traditional computers, quantum computing could both enhance security measures and pose new challenges for encryption protocols.
Organizations will need to adapt their digital identity systems to ensure they can withstand potential quantum threats.
Role of Machine Learning in Identity Fraud Detection
Machine learning algorithms are increasingly being utilized to detect and prevent identity fraud in real-time. By analyzing patterns and anomalies in user behavior, machine learning systems can identify suspicious activities and flag them for further investigation. As these algorithms continue to improve and evolve, they will play a crucial role in enhancing the security of digital identity protocols.
Self-Sovereign Identity and its Implications
Self-sovereign identity is a concept that empowers individuals to have control over their own digital identities without the need for intermediaries. By leveraging blockchain technology and decentralized systems, self-sovereign identity solutions offer enhanced privacy, security, and user control. This approach could revolutionize the way digital identities are managed, putting individuals at the center of the identity verification process.
Last Point
As we conclude this riveting discourse on Implementing Safe Digital Identity Protocols in 2025, one thing becomes abundantly clear - the future of cybersecurity hinges on the proactive measures we take today. Embrace the possibilities, fortify your defenses, and step boldly into a digital landscape where security is not just a priority, but a way of life.
Frequently Asked Questions
What are the potential risks of not implementing safe digital identity protocols?
Without secure digital identity protocols, individuals and organizations are vulnerable to identity theft, data breaches, and unauthorized access to sensitive information.
How do blockchain and biometrics enhance digital identity security?
Blockchain ensures tamper-proof records, while biometrics provide unique physical identifiers, making authentication more secure and reliable.
What role does GDPR play in digital identity protocols?
GDPR mandates data protection and privacy for EU citizens, impacting how digital identities are managed and secured.
Why is user-centric design important in digital identity systems?
User-centric design ensures that security measures are seamlessly integrated into user experiences, enhancing usability without compromising safety.






![5 Best eCommerce Marketing Digital Agencies [2024 Edition]](https://share.radartasik.id/wp-content/uploads/2025/08/Best-E-Commerce-Marketing-Agencies-2048x1024-1-120x86.jpg)